Security: Page 7
-
CISOs still expect cyber budget increases amid economic pressure
Security executives continue to focus on maximizing value as they seek a more efficient and simplified security posture, according to a report from Nuspire.
By David Jones • June 1, 2023 -
Palo Alto Networks teases plans for generative AI across security services
The security vendor is taking a restrained approach to deploying generative AI products, but the company’s leaders still believe the technology will herald a major shift for cybersecurity.
By Matt Kapko • May 31, 2023 -
 Explore the Trendline➔
Explore the Trendline➔
 jariyawat thinsandee via Getty Images
jariyawat thinsandee via Getty Images Trendline
TrendlineIT Security
Security strategies benefit from nimbleness as companies respond to high-profile vulnerabilities and support internal talent gaps.
By CIO Dive staff -
Cyber resilience programs fall short on preparing workers for a crisis
The report from Immersive Labs raises questions about whether corporate employees would know how to respond after a major cyberattack.
By David Jones • May 30, 2023 -
Why and how to report a ransomware attack
The majority of ransomware attacks go unreported, creating a blind spot that hampers response, recovery efforts and the prevention of future attacks.
By Matt Kapko • May 19, 2023 -
Why cyber is also a CIO problem
When an incursion occurs, IT teams need to have a recovery plan and backup systems ready for deployment.
By Matt Ashare • May 18, 2023 -
SolarWinds turns to Infosys to accelerate SaaS shift
The move eases the transition from on-prem to cloud-based software that was already underway, President and CEO Sudhakar Ramakrishna said.
By Matt Ashare • May 11, 2023 -
White House considers ban on ransom payments, with caveats
Experts suggest the effort, a reversal from the administration's previous stance, is fraught with complications that could cause unintended consequences.
By Matt Kapko • May 8, 2023 -
How 7 cybersecurity experts manage their passwords
What do CIOs and other cyber experts do to manage credentials? Hint: they don’t reuse passwords.
By Matt Kapko • May 4, 2023 -
Software industry leaders debate real costs and benefits of CISA security push
The global effort toward secure by design is seen as a potential game changer for software security, but may require investments and cultural changes.
By David Jones • April 17, 2023 -
There’s a movement afoot to make tech vendors responsible for cybersecurity
The international joint guide to secure by design encapsulates security recommendations long-touted by CISA, including technical tactics for software and infrastructure design.
By Matt Kapko • April 13, 2023 -
How Target approaches identity and access management
Designing an IAM system that provides a good user experience while preventing unauthorized access is a critical responsibility.
By Matt Kapko • April 12, 2023 -
Leftover data lurks in the enterprise, creating business risk
When an organization has little data visibility, it becomes even more vulnerable to leaks and breaches — as well as insider and external threats.
By Sue Poremba • April 11, 2023 -
Samsung employees leaked corporate data in ChatGPT: report
Data privacy is a concern for companies with employees using ChatGPT’s web-based interface, as input data is used to train and improve the tool.
By Lindsey Wilkinson • April 7, 2023 -
IT security leaders still told to keep data breaches quiet, study finds
Bitdefender research found 7 in 10 IT and security professionals in the U.S. have been asked to keep a breach confidential.
By David Jones • April 6, 2023 -
Upskilling, reskilling central to competing for tech talent, survey finds
Leading organizations were more likely than their peers to put in place upskilling or reskilling initiatives, a report from NTT DATA found.
By Roberto Torres • April 4, 2023 -
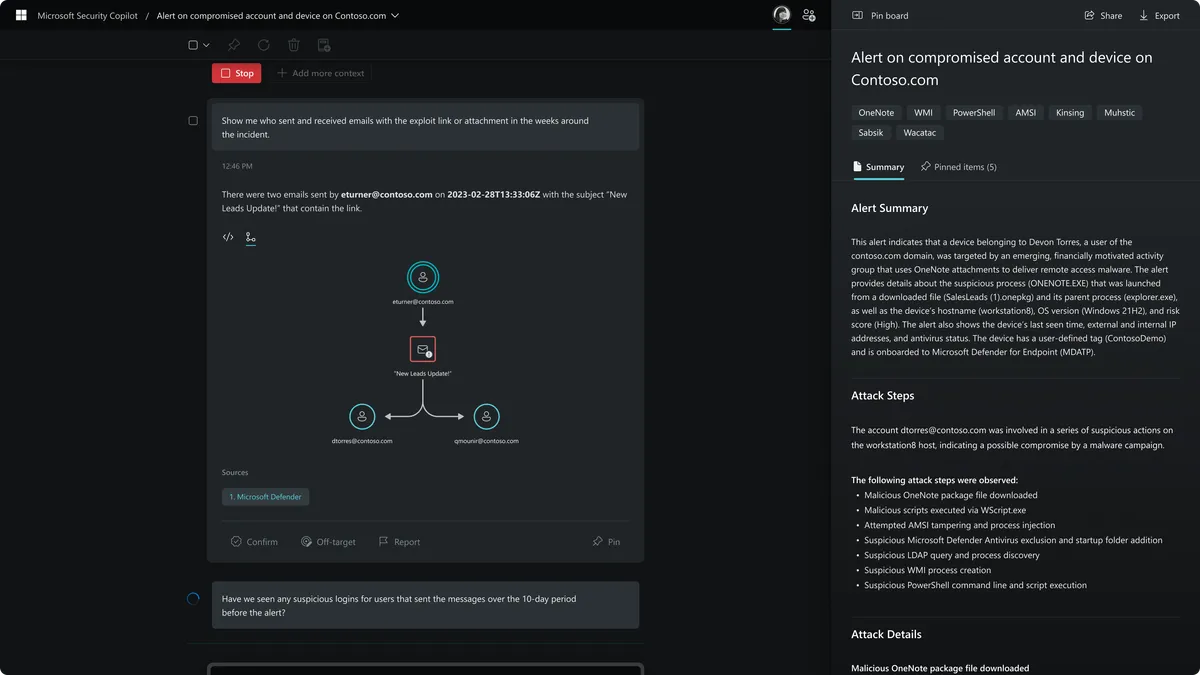
Microsoft unveils Security Copilot built on GPT-4
The technology combines OpenAI's generative AI capabilities with Microsoft's threat intelligence and security network.
By David Jones • March 28, 2023 -
Deep Dive
Tech vendor risk raises vetting stakes in wake of SVB crisis
Deposits are safe, but tech startups may no longer have access to venture debt and the lines of credit that helped fuel innovation.
By Matt Ashare • March 27, 2023 -
5 tips to counter identity and access management risks
Many organizations rely on identity and access management tools for credential management and authentication. But these systems aren’t foolproof.
By Matt Kapko • March 24, 2023 -
ChatGPT bug underlines need to limit shadow IT
If you share information with the tool, you do so at your own risk, according to experts.
By Lindsey Wilkinson • March 23, 2023 -
FTC opens inquiry into cloud market competition, security
As consolidation among hyperscalers grows, federal authorities are raising concerns over cloud dependence in critical sectors.
By Matt Ashare • March 22, 2023 -
Ill-prepared against cyberattacks? You’re not alone, Cisco says
The cybersecurity readiness gap looms large, and smaller organizations were ranked the least prepared.
By Matt Kapko • March 22, 2023 -
Security drives software purchases for half of US companies
The study from Capterra comes weeks after the U.S. announced plans to shift liability for weak product security onto the tech industry.
By David Jones • March 21, 2023 -
Workforce reductions hinder tech upskilling: report
As layoffs and hiring freezes reach tech companies, funding and scheduling training becomes a problem, a Pluralsight report found.
By Matt Ashare • March 20, 2023 -
Cybersecurity market confronts potential consequences of banking crisis
Bank seizures impose new challenges on vendors in every segment — and may spur consolidation.
By Matt Kapko • March 17, 2023 -
Bank failure panic fuels moment of opportunity for threat actors
Threat hunters and security executives warned organizations to look out for malicious activity as regulators step in to operate Silicon Valley Bank.
By Matt Kapko • March 15, 2023