Security: Page 36
-
What to know about Zscaler, Wall Street's latest tech darling
The 10-year-old company was built on the premise that security needed to reflect how users interact with applications as technology shifted away from the data center.
By Naomi Eide • March 19, 2018 -
Intel CEO: We're addressing Meltdown, Spectre flaws with hardware 'partitions'
As for software updates, 100% of impacted Intel products from the last five years have been issued microcode updates.
By Samantha Schwartz • March 16, 2018 -
 Explore the Trendline➔
Explore the Trendline➔
 jariyawat thinsandee via Getty Images
jariyawat thinsandee via Getty Images Trendline
TrendlineIT Security
Security strategies benefit from nimbleness as companies respond to high-profile vulnerabilities and support internal talent gaps.
By CIO Dive staff -
Deep Dive
4 answers you need to know about the dawn of 1Tbps DDoS attacks
Historically smaller DDoS attacks were not able to harness the same kind of bandwidth accessible to memcached servers seen in the recent attacks.
By Samantha Schwartz • March 15, 2018 -
Is biometric authentication really better than traditional passwords?
Resistance to adopt biometric technologies stems from cost, reliability, upgrade requirements and concerns over where the biometric data will be stored.
By Samantha Schwartz • March 13, 2018 -
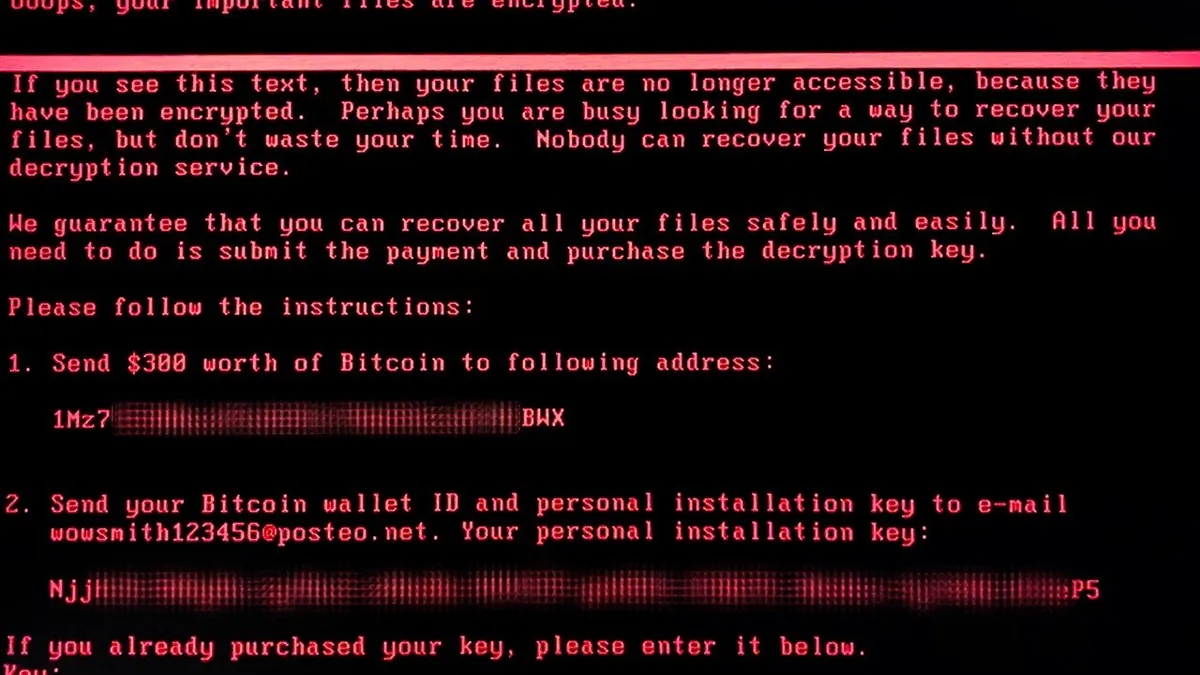
What nightmares run on: Robots are vulnerable to ransomware too
Traditional ransomware targets and encrypts a data. But ransomware for robots encrypts and blocks the software they run on, stalling operations.
By Samantha Schwartz • March 12, 2018 -
2017 cyberattack victims calling on industry for action, Microsoft president says
Tech companies that inadvertently created the very platforms used as vehicles for cyberattacks have a new set of responsibilities in cybersecurity.
By Samantha Schwartz • March 9, 2018 -
Deep Dive
GDPR puts the spotlight on compliance MVPs: Data protection officers
For companies still in the early stages of the compliance journey, looking at DPOs already hard at work on GDPR compliance can help get the process started.
By Alex Hickey • March 8, 2018 -
Hackers are creating 'web dossiers' by looking at your browser history
Hackers can personalize attacks based on an individual's visited sites, HTTP cookies, LocalStorage, saved credentials and autofill features on browsers.
By Samantha Schwartz • March 7, 2018 -
Take a seat GitHub: Service provider suffers record 1.7Tbps DDoS attack
Despite the massive attack, no outages were reported by the targeted service provider.
By Samantha Schwartz • March 6, 2018 -
Deep Dive
How Maersk proved its 'herculean resilience' after malware devastation
For 10 days following Nyetya, the shipping giant operated without reliable IT and had to keep the lights on while overhauling basic infrastructure.
By Samantha Schwartz • March 6, 2018 -
Deep Dive
Look out, big tech: FTC nominees eye Silicon Valley for antitrust regulation
At the committee hearing, tech was a focus of all four nominees, who will undergo a confirmation vote in the Senate later this year.
By Alex Hickey • March 5, 2018 -
Equifax breach costs: $114M and counting
The company also announced Thursday that an additional 2.4 million U.S. consumers were impacted by its breach.
By Alex Hickey • March 2, 2018 -
GitHub's record DDoS attack leads us further into '1Tbps DDoS era'
The company suffered a 1.35Tbps DDoS attack followed by a 400Gbps spike earlier this week but was quick to rebound.
By Samantha Schwartz • March 2, 2018 -
70% of cybersecurity professionals are 'open' to a job change
Security experts are not afraid to leave their current job, especially if the C-suite will take their advice into consideration.
By Samantha Schwartz • March 1, 2018 -
Deep Dive
US v. Microsoft: How do you rule on the cloud when legislation is over 30 years old?
Supreme Court justices wrangled with federal and Microsoft attorneys at Tuesday's arguments, fixating on legislation in the works to address the outdated SCA and what locations are relevant to data disclosure.
By Alex Hickey • Feb. 28, 2018 -
Fraud, cyber and insider threats plague businesses as incidents reach all-time high
The risk of fraud has never been greater, according to a new report from Kroll, and survey respondents feel more vulnerable than ever.
By Naomi Eide , Dan Alaimo • Feb. 27, 2018 -
Mobile ransomware skyrockets 415% in 2017 on the heels of WannaCry's success
Mindless hacking is retiring as more targeted attacks took precedent in 2017.
By Samantha Schwartz • Feb. 27, 2018 -
Deep Dive
To strategically increase your city's cyber resiliency, take a page from Rotterdam
The city of Rotterdam leads the way internationally on cyber resiliency in its port system, which relies extensively on automation and digitization of logistics operations.
By Chris Teale • Feb. 22, 2018 -
Expect hackers to build off of WannaCry, Nyetya in 2018
Hackers are finding new ways to navigate through a network, including manipulating existing malware strategies to self-propagate, according to a Cisco report.
By Samantha Schwartz • Feb. 21, 2018 -
US spent up to $109B on cybercrimes in 2016. How much will it spend in 2018?
The White House officially declared the Russian military responsible for last year's Nyetya wiper.
By Samantha Schwartz • Feb. 20, 2018 -
Will GDPR lead to an uptick in ransomware?
CEOs were the most spoofed and CFOs were the most targeted by business email scams in 2017, according to a Trend Micro report.
By Alex Hickey • Feb. 20, 2018 -
Intel ups bug bounty payouts to $250K
The company is opening up its bug bounty program to all security researchers and prioritizing hardware flaws over firmware and software vulnerabilities
By Naomi Eide • Feb. 15, 2018 -
Deep Dive
100 days to GDPR: How Box got ready
Companies need to begin looking at data protection as a combination of data security and data privacy, according to Crispen Maung, VP of compliance at Box.
By Alex Hickey • Feb. 14, 2018 -
Equifax taps Home Depot's CISO to retool security
What's key for Equifax is to fully understand its networks and install a security strategy that can patch and respond to threats in a timely manner.
By Naomi Eide • Feb. 13, 2018 -
Deep Dive
Technology of love: Between the sheets of OkCupid's amorous applications
Big data, the cloud, cybersecurity and software may play a bigger role in your love life than you think.
By Alex Hickey • Feb. 13, 2018