Security
-
Bipartisan bill seeks extension to cyber threat info-sharing
Two federal lawmakers proposed a renewal of the Cybersecurity Information Sharing Act of 2015, which is due to expire in September.
By Elizabeth Montalbano, Contributing Reporter • April 18, 2025 -
Aviation sector faces rising cyber risks due to vulnerable software, aging tech
A report published Thursday called on federal authorities to conduct comprehensive risk assessments and take steps to modernize the air traffic control system.
By David Jones • April 15, 2025 -
 Explore the Trendline➔
Explore the Trendline➔
 jariyawat thinsandee via Getty Images
jariyawat thinsandee via Getty Images Trendline
TrendlineIT Security
Security strategies benefit from nimbleness as companies respond to high-profile vulnerabilities and support internal talent gaps.
By CIO Dive staff -
Remote access tools most frequently targeted as ransomware entry points
Supply chain risk via third-party vendors increased sharply in 2025, according to a report by At-Bay.
By David Jones • April 14, 2025 -
CIOs worry about cyber threats, tech talent
Tech executives grapple with a looming skills gap as they juggle cybersecurity with the speed of innovation, according to an Experis survey.
By Nicole Laskowski • April 11, 2025 -
AI agents emerge as potential targets for cyberattackers
Digital entities, including bots and agents, pose a growing cybersecurity risk for enterprises, researchers found.
By Alexei Alexis • April 8, 2025 -
Where enterprises go wrong with cloud networking
While most companies have figured out how to migrate data without incurring huge fees, getting it back can be costly, according to Forrester.
By Matt Ashare • April 3, 2025 -
Enterprises beef up cybersecurity plans to mitigate AI risks
More than 2 in 5 leaders say they’ve strengthened practices to curb increased threats, misuse and other vulnerabilities tied to using the technology.
By Lindsey Wilkinson • March 28, 2025 -
What’s keeping technology leaders up at night?
From skill gaps and governance hurdles to the rush of AI advancements, executives from Mondelēz, EY, Walmart and other enterprises share what worries them.
By Lindsey Wilkinson • March 26, 2025 -
Google acquisition of Wiz driven by enterprise embrace of multicloud
The combined security platform will expand Google’s reach across a range of major cloud environments.
By David Jones • March 19, 2025 -
Trump nominates Plankey to lead CISA
Sean Plankey previously held key roles at the Department of Energy and National Security Council during the first Trump administration.
By David Jones • March 11, 2025 -
Cyberattacks targeting IT vendors intensify, causing bigger losses
Ransomware criminals are on the hunt for prime targets that can yield bigger payouts, according to cyber risk management firm Resilience.
By Alexei Alexis • March 6, 2025 -
SEC revamps cyber, crypto enforcement unit under Trump administration
Analysts expect cyber risk disclosure rules to remain in place, despite a push for hands-off regulation from the Trump administration.
By David Jones • Feb. 24, 2025 -
Security tool consolidation boosts efficiency, threat mitigation
The controversial shift to integrated security platforms can pay off for enterprises, according to an IBM and Palo Alto Networks study.
By David Jones • Feb. 11, 2025 -
CISO stature gains traction as global cyber risk escalates
Security leaders are making inroads with corporate boards and now have a seat at the table with CEOs, a Splunk report shows.
By David Jones • Feb. 4, 2025 -
Cyber disruptions remain top business risk concern in US, globally
Global disruption caused by CrowdStrike’s IT mishap added to longtime concerns about data breaches and ransomware, according to Allianz.
By David Jones • Jan. 21, 2025 -
What CIOs should know as DORA regulations kick in
The EU’s Digital Operational Resilience Act requires banks and insurance companies to restore critical IT systems within two hours, starting Friday.
By Matt Ashare • Jan. 15, 2025 -
CISA director reiterates call for stronger cyber risk ownership
Jen Easterly said boards need to consider cybersecurity threats as core risks and fully incorporate them into corporate business strategy.
By David Jones • Jan. 13, 2025 -
Cyberattacks, tech disruption ranked as top threats to business growth
Two in 5 executives view data breaches and leaks as the most financially burdensome man-made threats, a Chubb study found.
By Alexei Alexis • Jan. 10, 2025 -
SaaS sprawl weighs down developers
Maintaining and updating interconnected applications shrinks the bandwidth of IT teams, according to Onymos.
By Matt Ashare • Dec. 18, 2024 -
More than half of leaders haven’t trained in AI, survey shows
A lack of training could negatively affect security, privacy and corporate competitiveness, General Assembly says.
By Carolyn Crist • Dec. 13, 2024 -
Executives see another CrowdStrike-level IT outage on the horizon
IT and business leaders admit to prioritizing security at the expense of service disruption readiness, a PagerDuty report found.
By Matt Ashare • Dec. 12, 2024 -
Sponsored by 10KMedia
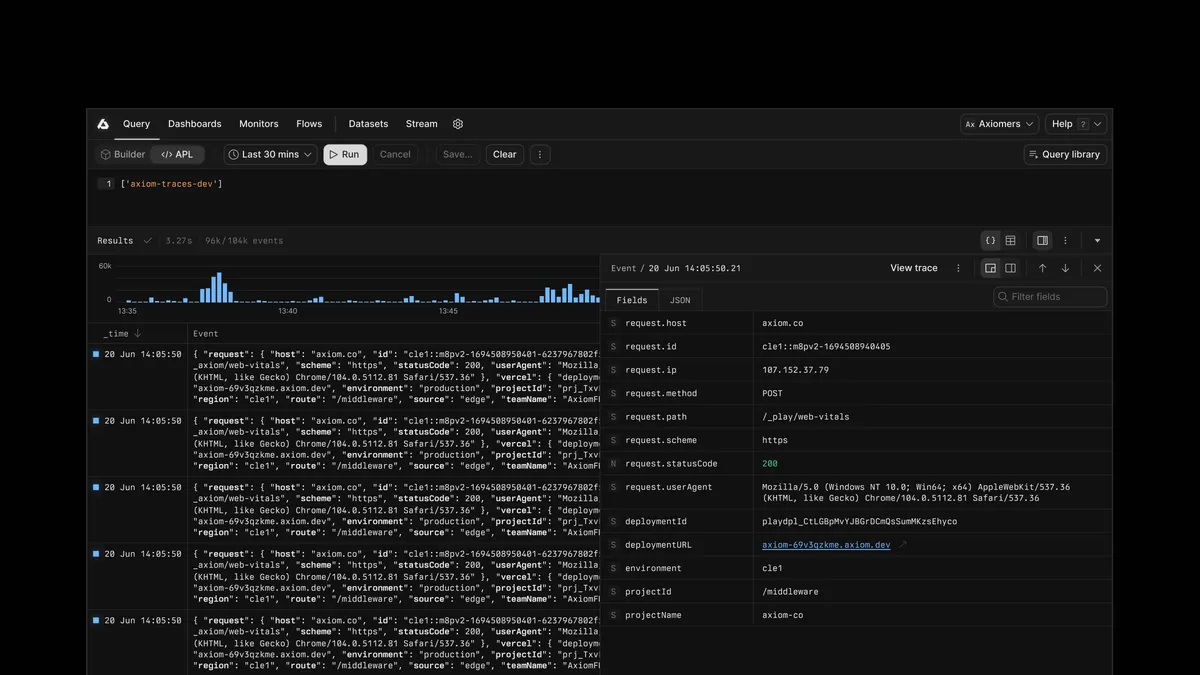
Logging 2.0 – Why logging needs to be re-imagined in the age of AI
With Axiom’s centralized datastore, high-scale engineering organizations don’t have to compromise on what to keep, what to keep warm (always querable), or where to store data.
By Dominic Chapman, Head of Product at Axiom • Dec. 10, 2024 -
Sponsored by Lumos
Securing identities in 2025 – The future of identity governance
2025 is near—are you ready for the evolving challenges of identity lifecycle management?
Dec. 9, 2024 -
For IT pros, the CrowdStrike crisis was a ‘call to arms’
The global outage triggered investments in people, processes and technologies to beef up enterprise resilience, Adaptavist research found.
By Matt Ashare • Dec. 5, 2024 -
CrowdStrike avoids customer exodus after triggering global IT outage
The cybersecurity vendor reported $33.9 million in expenses related to the July 19 incident, which caused the company to swing to a loss.
By Matt Kapko • Nov. 27, 2024