In an era of escalating cyber threats, safeguarding sensitive information, especially personally identifiable information (PII), has become a critical challenge for businesses rich in customer data across all sectors. Despite the cybersecurity industry's explosive growth to $200 billion annually, data breaches continue to make headlines. This paradox begs the question:
Ever wonder why we keep buying more security but don't feel more secure?
The answer lies not in adding more layers of protection, but in fundamentally rethinking our approach to data architecture. What if your company's most sensitive data became useless to hackers, even if they breached your systems?
Enter the data privacy vault: A new approach to safeguarding PII, moving beyond traditional security measures. This emerging new architecture for PII protection simplifies the challenges companies typically face when protecting sensitive data. Adopting this can provide a robust, scalable solution to protect PII - reducing risk of exposure while maintaining data utility for business operations.
The growing threat of data breaches
In just three months from June to August 2024, 241 new data breaches exposed the PII of over 35.8 million people– costing companies millions and eroding consumer trust. This year, the average cost of a data breach in the U.S. reached a staggering $9.36 million according to IBM.
These sobering statistics highlight the urgent need for robust data protection measures. Yet, many companies still struggle to safeguard sensitive information like PII effectively. Consumer studies have found that 71% of consumers would stop doing business with a company that mishandled their data.
This underscores the critical link between data privacy and customer loyalty. The root cause of many data breaches lies in a fragmented approach to data security. Simply buying more tools won't fix the problem. Traditional security measures, such as firewalls and encryption, are no longer sufficient to protect against sophisticated cyber attacks.
We need to rethink how we build our data infrastructure and what it means to secure our customers' data. The proliferation of data across various platforms – including data warehouses, data lakes and now large language models (LLMs) – has expanded the attack surface, making it increasingly challenging to secure PII.
The problem is PII
Not all data is created equal. Some data, like PII, is special and more valuable than other forms of data. PII is at the heart of many data breaches. This sensitive data, including names, birthdates and social security numbers, is highly valuable to cybercriminals. Protecting PII is challenging for several reasons.
First, many organizations struggle to identify and locate all the PII within their systems.
Second, PII often gets duplicated and spread throughout an organization (PII data sprawl), creating multiple potential vulnerabilities. Additionally, both malicious insiders and external cybercriminals pose serious threats to PII data. Comprehensive access controls and monitoring is essential but often difficult to implement across fragmented systems.
Lastly, the ever-evolving landscape of data privacy regulations like GDPR, CCPA and HIPAA presents a critical challenge, adding another layer of complexity to data protection efforts. Companies must not only protect data but also demonstrate compliance with these complex and often overlapping laws. This includes implementing data handling procedures, maintaining audit trails and being prepared for regulatory audits. Failure to comply can result in hefty fines, legal consequences and damage to reputation.
The solution is a data privacy vault
To address the above PII challenges, privacy-first companies are adopting a new architectural pattern known as the data privacy vault. This approach, recommended by IEEE as the future of privacy engineering, involves isolating, protecting and governing access to sensitive customer data. The data privacy vault architecture separates PII from other data stores, creating a secure and isolated environment where sensitive information is stored and protected. This approach effectively de-risks existing application and analytical systems by transforming PII in those layers into de-identified tokens that carry no sensitive data, addressing the root cause of many data breaches.
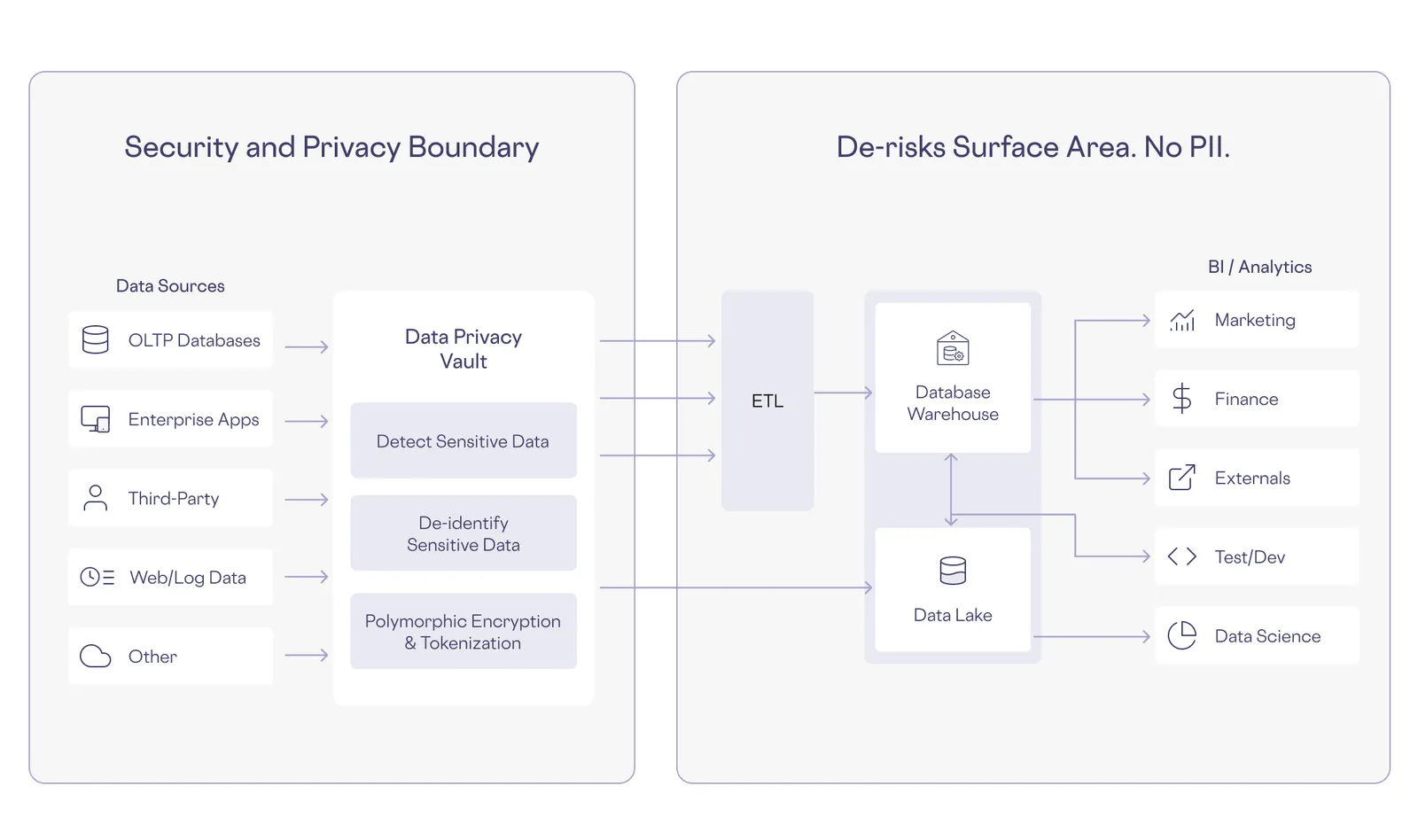
How it works?
The data privacy vault has evolved from legacy data protection methodology in four key ways:
- Isolation: PII is stored separately from other systems, reducing the attack surface.
- Protection: Advanced encryption and tokenization techniques secure the data within the vault.
- Governance: Fine-grained access controls ensure that only authorized users and systems can access specific data elements.
- Polymorphic Encryption: This proprietary technology allows for secure yet functional data handling, enabling operations like querying and analytics without exposing PII.
Benefits of implementing a data privacy vault
As organizations look to secure their data infrastructure, adopting a data privacy vault offers significant advantages:
- Enhanced Security: By isolating and protecting PII, the risk of exposure in the event of a breach is significantly reduced.
- Improved Data Utility: Advanced techniques like polymorphic encryption and tokenization allow organizations to perform analytics and other operations on protected data without compromising security.
- Simplified Compliance: Centralized storage and governance of sensitive data make it easier to adhere to various data protection regulations.
- Reduced Risk in Analytics and AI: The data privacy vault can integrate with data warehouses and LLMs, allowing for secure use of sensitive data in advanced analytics and AI applications.
- Scalability: The data privacy vault architecture can adapt to evolving threats and business needs, future-proofing data protection strategies.
GoodRx: A new standard for healthcare privacy
GoodRx, the leading prescription savings platform in the U.S, faced challenges in securing billions of prescription claims containing sensitive patient information. They needed a solution that could protect this data while maintaining its utility for analytics and customer support operations.
Implementing Skyflow Data Privacy Vault allowed GoodRx to secure millions of patient records containing PII and Protected Health Information (PHI). The solution maintained backward compatibility with existing tokenized data and put in place fine-grained access controls for different user groups and applications. Additionally, it improved performance through distributed data storage and querying capabilities, while preparing for secure integration with LLMs. As Nitin Shingate, CTO of GoodRx, noted, "We were able to successfully deploy Skyflow in less than three weeks with the zero-trust vault architecture, and our total cost of ownership decreased by 67%." This rapid implementation and cost-effectiveness highlight the efficiency and value of Skyflow's solution for GoodRx.
The implementation process proved significantly faster and more cost-effective than building an in-house solution. GoodRx initially attempted an in-house build, dedicating 6 months and 10 engineers to the project. But the complexity of building a data privacy vault loomed large, with another 18 months needed just to reach the minimum viable product (MVP). Recognizing the need for a more efficient and effective approach to building a data privacy vault, GoodRx pivoted. They partnered with Skyflow, a decision that proved both swift and savvy. This collaboration not only fast-tracked their security goals but also positioned them at the forefront of data protection. The result? A cost-effective solution that met their stringent standards and set the stage for future innovations. GoodRx's story showcases how sometimes, the smartest move is knowing when to seek expertise rather than reinventing the wheel.
What’s your data protection strategy for 2025 and beyond?
As organizations continue to collect and leverage vast amounts of sensitive data, the need for robust protection measures will only grow. The data privacy vault architecture represents a paradigm shift in how we think about data security, moving from perimeter-based security to holistic data protection.
In an era when data breaches are becoming increasingly common and costly, the data privacy vault offers a powerful solution for safeguarding sensitive information. By isolating and securing PII at its source, organizations can significantly reduce their risk exposure while maintaining the ability to derive value from their data. As technologies like AI and LLMs become more prevalent, the ability to use sensitive data securely will become a critical competitive advantage.
With this approach, organizations can enhance their security, simplify compliance efforts and unlock the full potential of their data – all while protecting the privacy of their customers.
As you consider your organization's data protection strategy for 2025, ask yourself:
Is it time to vault your most valuable asset – your customers' data?










