UPDATE: More details emerged about the strain of ransomware spreading across Europe and into the U.S. Wednesday as researchers scrambled to respond. Security researchers have agreed that the ransomware is a strain of Petya, leading to an array of names. Kaspersky Lab initially called it NotPetya, but later began referring to it as ExPetr. Cisco’s Talos is referring it to as Nyetya, though others are calling it Petrwrap and GoldenEye, according to Talos.
Though experts are still looking into the distribution and initial attack vector, Kaspersky found that a Ukrainian website was hacked and "used to distribute the ransomware to visitors via a drive-by-download of the malicious file," the security firm said in a statement. No specific exploits were used to infect systems, but rather "visitors were served with a malicious file that was disguised as a Windows update."
Unlike last month’s WannaCry, there is no known killswitch yet, meaning the ransomware could continue to spread as more systems go online.
Dive Brief:
- A rash of ransomware spread globally Tuesday, impacting scores of companies across sectors. Marketing company WPP, snack giant Mondelēz International and shipping company Maersk were just some of the companies reporting IT outages, with WPP and Maersk blaming the downed systems on a cyberattack. Researchers are still ascertaining the impact, scope and root malware strain underlying the attack.
- About 2,000 users were attacked so far, concentrated in Russia and Ukraine, according to Kaspersky Lab. The cybersecurity firm also registered attacks in Poland, Italy, in the United Kingdom, Germany, France and the U.S. The number of victims and geographical scope of the attack will likely evolve over time as connected systems become infected, said Vincent Weafer, VP of McAfee Labs, in a statement to CIO Dive.
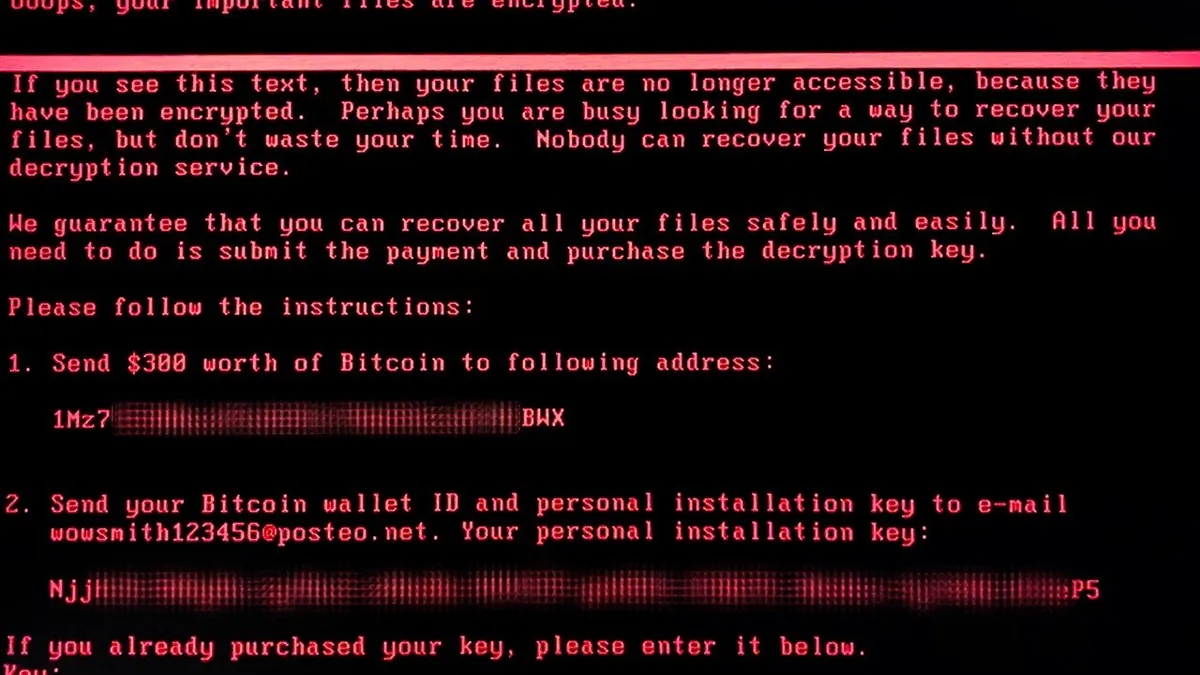
- Once targeted, victims were greeted with a message stating "ooops, your important files are encrypted," according to a Kaspersky screen shot. The message declared victims could easily recover files by paying $300 in Bitcoin as payment for a decryption key and receive a decryption key via email. However the email service provider, Germany-based Posteo, blocked the attacker's account, thereby blocking victims' access to a decryption key, Motherboard reports.
Dive Insight:
Researchers are still locking down what strain of ransomware is causing the attack, but early reports have confirmed it is not Petya as previously reported. In response, researchers at Kaspersky have named it "NotPetya."
From what researchers can tell right now, the malware is spreading via the EternalBlue exploit and through email using a form of office document, said Daniel Smith, security researcher at Radware, in a statement to CIO Dive. The EternalBlue exploit was also at the heart of the WannaCry ransomware attacks in May.
Experts are quick to compare large-scale cyberattacks, looking at the scope of attacks and how quickly ransomware spreads and is contained. Though ransomware victims' operations are interrupted, by restoring from backups, organizations can regain operations.
The kicker with this attack is the small demand. Malicious actors are likely to see a higher return for their efforts because $300 in bitcoin is small ask to allow victims to resume operations. Rather than launch crippling ransomware attacks with large demands, launching a large-scale attack with a small ransom might increase cybercriminal's ROI. Had a researcher not discovered a kill switch, the WannaCry ransomware with a ransom price of just $600 in bitcoin might have netted attackers far more than the $26,000 they reportedly received.
But if paths to contact the attackers is severed, it is likely many ransomware victims will not pay up.
Starting with the ransomware attack against Hollywood Presbyterian Medical Center last February there has been a drastic uptick in the number of ransomware attacks. More attackers are unleashing exploits to get organizations to pay up, and ROI has increased greatly. In 2016, organizations paid roughly $1 billion for ransomware, up from $24 million in 2015.
While individual ransomware attacks used to be more common, global attacks are emerging as the new normal. With a deftly coded piece of malware, attackers can launch ransomware across networks to ensure the highest possible impact. Total defense against such attacks is practically impossible, however companies can prepare with disaster recovery measures and ensuring systems stay up-to-date.
Kaspersky's advice to those impacted is to manually update antivirus databases "immediately" and ensure all security updates for Windows are installed, especially the one that fixes bugs exploited by EternalBlue.